Andrés Valencia
PC Security
This page offers information and tools to keep your PC secure,
free of intrusions in the Internet.
- General Security Advice for Internet Users
- Anti-Spyware/Anti-Adware Online Scanners (including anti-Conficker)
- Expanded Threats: Spyware, Rootkits, Malicious JavaScript
- A Final Warning
General Security Advice for Internet Users
The Internet is a dangerous environment as proven by the frequent "Denial of Service" attacks, the infection of legitimate Web sites,
the "Worms" and "Trojan Horses" infecting computers to implement "remotely controlled" intrusions in networks
by means of infected and enslaved PCs; "robots", or "bots".
The computers with the highest risk of infection are those with a permanent connection to the Internet.
Bots work silently, but we all see their work. Almost every spam e-mail is sent from a hijacked computer. Every time you receive a spam, a hijacked computer sent it.
Your PC is not necessarily the final target in these attacks: If infected,
it is used to attack other computers and disseminate the infection.
The attempted dissemination activity congests the Internet, in particular e-mail transit.
The unavailability of the infected computers can cause damage to people and property.
And you could be an involuntary co-responsible.
The most employed attack method is the exploitation of "vulnerabilities" in the operating system or networking software
to install malignant non-authorized programs ("Malware") in your computer.
A Web site knows the IP (Internet Protocol) address of the PC from where you are viewing it,
and could test your PC for vulnerabilities. If a vulnerability is found, an infected Web site could exploit it.
Once infected, a simple firewall (like the one in Windows XP) would not be a defense,
as it is the Malware in your computer that will be requesting the traffic.
A complete firewall would not be a defense either,
if you grant permission to communicate to unknown software that has already infected your PC.
If your PC has a vulnerability, and you visit an infected site that can exploit it, your PC could be enslaved. Backdoor and key-logger programs could be installed, and a remote attack on another computer be launched from your PC.
If your Web browser has been infected by "Adware" so it makes automatic visits to unknown sites (pop-up advertising), its vulnerabilities could be exploited. See Spyware, further down in this page.
To eliminate your vulnerabilities keep your operating system and networking software updated
(Web browser, mail program, etc.).
In the MS Internet Explorer menu: Tools,
Windows Update.
Or visit Microsoft Update.
Install all Critical and Security Updates as soon as possible.
Microsoft releases them on the second Tuesday of every month.
However, if a security threat occurs, such as a widespread virus or worm that affects Windows-based computers,
Microsoft will release a corresponding update as soon as possible.
Other types of updates can be released whenever they are ready.
Service Packs SP1 and SP2 are free, but only available automatically to legitimate Windows XP users.
Install all Service Packs.
If your PC clone came with an illegal copy of Windows,
you can buy and install an original without loosing your installed programs or your documents.
If you can not install and update a legal copy of MS Windows on an Internet-connected PC,
it is possible that your vulnerabilities will be exploited even if you use a complete firewall program.
Get your updates from The Software Patch
(Download site for patches, upgrades, service packs and hardware drivers).
Do not use an unsupported version of Windows; its vulnerabilities represent a grave security risk.
Regularly update your Microsoft Office programs: visit Microsoft Office Online and select "Office Update", or visit Microsoft Update. Microsoft releases these updates on the fourth Tuesday of each month. Have your original MS Office installation disks on hand.
The Secunia Personal Software Inspector (PSI)
is a free computer security solution that identifies vulnerabilities in applications on your private PC.
Vulnerable programs can leave your PC open to attacks.
Simply put, it scans software on your system and identifies programs in need of security updates to safeguard your PC against cybercriminals.
It then supplies your computer with the necessary software security updates to keep it safe.
Using a scanner like Secunia PSI is complementary to antivirus software, and as a free computer security program,
is essential for every home computer.
Home users should download and install the
Secunia Personal Software Inspector (PSI).
Download and run the
Microsoft Baseline Security Analyzer (MBSA),
an easy-to-use tool that helps determine your security state in accordance with Microsoft recommendations
and offers specific remediation guidance.
Improve your security management by using MBSA
to detect common security misconfigurations and missing security updates on your computer.
The Microsoft Baseline Security Analyzer (MBSA) is free,
but only available to legitimate Windows 2000, XP, 2003, Vista and Windows 7/8/8.1 users.
If you must run a vulnerable program, use the
Enhanced Mitigation Experience Toolkit (EMET)
from Microsoft (free) to help prevent the vulnerabilities from being exploited.
EMET uses security mitigation technologies and is designed to work with any software.
Considering that exposure to a single malicious site can turn your PC into a robot,
a spam generator or a slow performer, and steal login information;
securing your Web search activities is an important function.
Simply visiting a bad, hacked Web page can expose your machine.
Vulnerabilities and exploits
continue to permit hackers to spread rootkits and open backdoors on computers around the world.
Threat Labs Site Reports is AVG's latest security tool,
continuing our commitment to malware and virus detection and eradication.
Viral threats and malware have become more sophisticated so AVG's approach to proactive Internet security has shifted gears appropriately.
AVG Threat Labs provides a new way for users to benefit from over a million domain reports
and evaluate websites before they jeopardize their personal information.
[In the box, enter the address of the Web site you want to check, like for example oarval.org]
Make sure your computer is not sharing anything over the Internet.
This is especially important if you are using a permanent connection.
Avoid printer sharing over a LAN running on the TCP/IP protocol,
from the computers capable of directly connecting to the Internet.
(Control Panel, Network Connections, Local Area Connection Properties, General:
Do not check "File and Printer sharing for Microsoft Networks")
But if you must share files over the Internet, do not share whole drives;
only share expressly prepared, password-protected and "Read-only" folders with the required files.
Password-protected folders are available in Windows XP Professional.
In particular, never share the drive or the folder were the Operating System resides.
In Windows XP Home, share only temporarily, for the shortest period of time.
For example, create a folder named "Out" in "My Documents" and share it,
but do not check "Allow network users to change my files" (Properties, Sharing).
Using this system, all network users will be able to download files from the others Out folders,
but no one would be able to upload files to another computer.
This minimizes the possibilities of intrusion, but not of data theft.
Password protection minimizes both and should be used additionally.
In Windows XP Home, share only temporarily, for the shortest period of time.
Consider that some e-mail viruses fake the sending address to gain your confidence and
get you to execute an attached program, believing it to come from a known address.
Configure your e-mail program for high security.
In the MS Outlook Express menu: Tools, Options, Security: Restricted sites zone (More secure).
You should also select to "Warn me when other applications try to send mail as me".
Configure your antivirus program to examine the contents of your e-mail.
Never open or execute attachments before they are examined by your (recently updated) antivirus program!
No computer should be connected to the Internet without antivirus software of the highest quality, recently updated,
and configured for maximum security, that is, checking all files on entry, from any source.
Install an antivirus program, like the
Comodo Internet Security, or the
AVG Anti-Virus Free Edition
from Grisoft (in various languages).
If you use Windows 8, Windows 7, Windows Vista or Windows XP SP2, you can install a complete security program, like the
Comodo Internet Security
(Free), offering complete protection from Hackers, Virus, Spyware, Trojans and Identity theft,
and a Host Intrusion Prevention System that stops malware from being installed.
An extensive white list database of trusted applications helps reducing the number of initial alerts after installation.
The Firewall and Antivirus components can be installed separately.
[Best results in the
Matousec Proactive Security Challenge 64]
By installing malware (short for MALicious softWARE) on a machine, computer crackers can go anywhere, see and do anything they want with your computer, including banking records and your most intimate and personal documents. In addition to wreaking havoc with your machine and pillaging your personal property, some malware, specifically trojan horse servers, can even record your personal conversations if you have a microphone connected to your computer. Malware can invade your system without you ever knowing it and are designed to elude firewalls by using ports which are not blocked by network "firewall" security software or proxy servers. Many of them disable the most frequently used antivirus and software firewalls.
The Outpost Security Suite FREE
is an easy-to-use personal security suite for Windows that helps protect your digital valuables against hackers and identity theft
by preventing unauthorized users from gaining access to your computer through a network or the Internet.
Outpost Security Suite FREE is a free version of Agnitum's Outpost Security Suite Pro.
Outpost Security Suite FREE protects against viruses, hackers and data theft - all you need to stay protected.
[Excellent results in the
Matousec Proactive Security Challenge 64]
Protect your PC with the Ad-Aware Free Antivirus+: (Free)
Protect your PC with the Ad-Aware Free Antivirus+ by Lavasoft - Protection from Virus, Spyware & Malware.
Combining our legendary anti-spyware with a powerful antivirus, Ad-Aware Free Antivirus+ enhances them with real-time protection, download protection and continuously updated filters against malicious URLs, providing top-of-the-line anti-malware protection for the casual computer user.
Analyze and clean your PC with the Emsisoft Anti-Malware:
Comprehensive PC protection against viruses, trojans, spyware, adware, worms, bots, keyloggers and rootkits. (Previously a-squared Anti-Malware)
2 cleaning programs in 1: Anti-Virus + Anti-Malware
When downloading, you'll get the full version including all protection features for 30 days for free. Afterwards the unpaid software switches to a limited freeware scanner mode that allows you to scan and clean your PC whenever you want, but does not include the protection features against new infections.
Install the Emsisoft Anti-Malware
The Conficker Worm shocked PC security experts. Millions of computers were supposed to have been infected.
The free program Emsisoft Emergency Kit
checks whether Conficker (or other worms) are present in a computer.
In the worst case, the free program can immediately remove the security risk.
See How to find and clean malware infections with Emsisoft Emergency Kit
Protect your PC with the Panda Internet Security 2015: (Free)
Protect your PC with the Panda Internet Security 2015 for Virus, Spyware, Hacking and Potentially Unwanted Tools, Security Risks and Suspicious files.
Protect your PC with Microsoft Security Essentials: (Free)
Microsoft Security Essentials - Guards against viruses, spyware, & other malicious software.
You can't use Microsoft Security Essentials with Windows 8.1. But if you want to protect a PC with an older version of Windows, you can use Microsoft Security Essentials to help guard against viruses, spyware, and other malicious software.
If you use Windows 7 or Vista,
you can activate the Internet Connection Firewall on the Internet connection of computers that connect directly to the Internet.
It will protect you against external (from the Internet) unauthorized access.
But this simple firewall does not fully protect you from exploitation of vulnerabilities.
Use: Control Panel, Internet Options, Connections, Settings, Properties, Advanced.
If you want a simple firewall that is very easy to configure, then you could use the Windows XP SP2 Internet Connection Firewall. But if you want more advanced control over the traffic that passes through your computer and you also want to block unauthorized outgoing traffic (traffic from your computer out to the Internet) then choose a complete personal firewall from another company.
Use only one firewall program and only one antivirus program at the same time in your PC.
Two firewall programs, or two antivirus programs, can interfere with each other and block your PC.
Install all Windows Critical and Security Updates
Keep your antivirus software updated
Use a complete Firewall
Visit a security evaluation site on the Web, such as Steve Gibson's
Gibson Research Corporation.
There you can run the ShieldsUP! tests to see how well your machine is protected (or not). (Free)
Visit Secunia and
SecurityFocus
for Security News, Articles & Advisories.
Download and install the
Secunia PSI (Personal Security Inspector)
to a assure all of your software is updated.
Also run the tests for vulnerabilities to Internet threats at PC Flank (Make sure you're protected on all sides).
Visit the site OnGuard Online of the U.S.A. Federal Government to read practical recommendations to help you be on guard against Internet fraud, secure your computer and protect your personal information.
See my Antivirus Information Section
Anti-Spyware/Anti-Adware Online Scanners
[Running an Online Scanner under Windows Vista in general requires accessing it with Microsoft Internet Explorer in Administrator mode: Select a start icon for Microsoft Internet Explorer with a right click, select Run as Administrator]
Analyze and clean your PC with the BitDefender QuickScan:
(Against Virus and Spyware. Free)
System Requirements:
- Microsoft Windows 10, 8.1, 8, 7, Vista, XP, Me, 98, NT or Windows 2000, 2003
- Microsoft Internet Explorer
- ActiveX and JavaScript must be enabled in your browser's security settings
Downadup (or Conficker) is a self-updatable network worm that takes advantage of a Windows vulnerability to spread.
Its removal is complicated by the fact that it blocks many known antivirus software and associated websites.
Conficker disables the Microsoft Windows Firewall service.
Visit Microsoft Update and install all Critical and Security Updates.
See An Analysis of Conficker (SRI Malware Threat Center, February 4, 2009)
See Microsoft Security Bulletin MS08-067 - Critical: Vulnerability in Server Service Could Allow Remote Code Execution (October 23, 2008)
BitDefender
is the first to offer a free online tool which disinfects all versions of Downadup.
This domain is the first to serve a removal tool without being blocked by the e-threat.
Determine if it is infected with the Downadup worm (known also as Conficker or Kido):
Remove Downadup (Powered by BitDefender)
The Microsoft Malware Protection Center has updated the Malicious Software Removal tool (MSRT).
This is a stand-alone binary that is useful in the removal of prevalent malicious software,
and it can help remove the Win32/Conficker malware family.
You can download the MSRT from either of the following Microsoft Web sites:
update.microsoft.com and/or
Microsoft Malicious Software Removal Tool.
See Virus alert about the Win32-Conficker.B worm (Microsoft Help and Support)
Microsoft Safety Scanner
Helps remove viruses, spyware, and other malicious software (Free)
Analyze your PC Security with the Symantec Security Check: (Free)
The Web-based Security Scan and Virus Detection will help ensure a safe and productive Internet experience for you and your family. Security Scan determines whether your PC is protected from hackers, viruses, and privacy threats. Virus Detection uses Symantec's virus detection technology to check for virus infections. After analyzing your PC's current level of protection, we'll show you how you can enjoy the Internet and protect yourself at the same time.
System Requirements:
- Microsoft Windows 8.1, 8, 7, Vista, 95/98/XP or Windows NT/2000, or Mac OS 8.1 or newer
- Microsoft Internet Explorer 5 or newer
[Macintosh: MS IE 4.5 or newer, or Safari 1.0 or newer] - Cookies must be enabled in your browser's security settings
- ActiveX and JavaScript must be enabled in your browser's security settings
- If you are going through a firewall, it must be configured to transmit browser information (user agent) to the Web server
- If you use the AOL browser, please upgrade to the latest version [Keyword: Upgrade]
Analyze your PC with the ESET-NOD32 AntiVirus - Online Scanner: (Free)
The ESET Online Scanner is a good free virus scan in the Web. A user-friendly, powerful tool, the ESET online antivirus utility can remove malware - viruses, spyware, adware, worms, trojans, and more - from any PC utilizing only a web browser. The AntiVirus - Online Scanner uses the same ThreatSense technology and signatures as ESET NOD32 Antivirus, which means it is always up-to-date.
ESET Online Scanner requires the following minimum system components:
- Hardware: 133MHz Intel Pentium processor or equivalent. At least 32MB of available RAM. At least 15MB of available disk space.
- Operating System: Microsoft Windows 8.1, 8, 7, 98/ME/NT 4.0/2000/XP and Windows Vista.
- Software: Microsoft Internet Explorer (IE) 5.0 or later.
- User Permissions: Administrator privileges required for Windows Vista installation.
Analyze and clean your PC with the Trend Micro HouseCall AntiVirus - Scan Online: (Free)
The Web-based HouseCall AntiVirus - Scan Online will help ensure a safe and productive Internet experience for you and your family. HouseCall uses Trend Micro's virus detection technology to check for and eliminate virus infections, spyware, worms and other malware.
System Requirements:
- Microsoft Windows 8.1, 8, 7, Vista, 95/98/XP or Windows NT/2000
- Microsoft Internet Explorer 4.0, Netscape 3.01 or newer
- ActiveX and JavaScript must be enabled in your browser's security settings
Analyze and clean your PC with the F-Secure Online Scanner: (Free)
The Web-based F-Secure Online Virus Scanner will help ensure a safe and productive Internet experience for you and your family. The Online Virus Scanner uses F-Secure's virus detection technology to check for and eliminate virus infections, spyware and rootkits.
System Requirements:
- Windows 8.1 / 8 (all editions), Windows 7 (all editions), Windows Vista (Service Pack 2), Windows XP (Service Pack 3)
- Microsoft Internet Explorer 6.0 or newer
- ActiveX and JavaScript must be enabled in your browser's security settings
Other Anti-Spyware/Anti-Adware Scanners:
You can get rid of the Spyware/Adware in your PC by using:
Spybot - Search&Destroy
- Detect & Remove Spyware (Free)
Malwarebytes Anti-Malware
- Detects & removes malicious software from your computer (with Free version)
IObit Malware Fighter
- Detects & removes hidden malware (with Free version)
Norton Power Eraser
- Detects & destroys threats to your computer (Free)
SpywareBlaster anti-spyware protection
- Prevents installation of spyware & unwanted software (Free)
These tools can all be installed in the same PC as they are basically scanners and will not interfere with each other
or an antivirus program.
This is recommendable as each specializes in a different kind of spyware.
Expanded Threats
Expanded Threats exist outside of commonly known definitions of viruses, worms, and Trojan horses
and may provide unauthorized access, and threats to system or data security,
and other types of threats or nuisances.
Expanded Threats may be unknowingly downloaded from Web sites, email messages, or instant messengers.
They can also be installed as a by-product of accepting the End User License Agreement
from another software program related to or linked in some way to the Expanded Threat.
Consider that an e-mail can show a faked sending (From:) address to gain your confidence and get you to execute an attached program or visit a link, believing it comes from a known address or person.
See Symantec Security Response - Expanded Threats
"Spyware" (Spy Software):
"Spyware" programs are applications that send information via the Internet to the creator of the spyware, or the publisher. Spyware usually consists of core functionality and functionality for information gathering. The core functionality appeals to users and entices them to install and use the spyware. The End User License Agreement (EULA) informs users of the information-gathering actions, but most users overlook this information. Information that is sent to the publisher is normally used for improved direct marketing purposes. The type of sent information differs depending on the spyware program. In order for the publisher to properly digest the gathered data, some spyware programs send a unique identifier with the gathered information. Users often overlook the information-gathering functionality of spyware, leaving them unaware that the spyware publisher is gathering data from their computers.
See The Dangers of Spyware in Symantec Security Response - White Papers (.pdf, Adobe Acrobat Reader)
Generally, if your Web browser has been infected by "Adware" (advertisement software, a type of "Spyware"), it will make automatic visits to unknown sites (pop-up advertising), and its vulnerabilities could be exploited.
"Spyware" is a relatively new kind of threat that many common antivirus applications do not cover well. More and more spyware is emerging that is silently tracking your surfing behavior to create a marketing profile of you that will be sold to advertisement companies and used to force your browser to visit unknown sites automatically.
See Symantec Security Response - Expanded Threats (Spyware)
In response to this new area of risk (which Symantec termed expanded threats)
Symantec began helping customers by enabling them to detect spyware and other undesirable programs on their computers
using the Norton AntiVirus product.
Times have changed considerably and Symantec's approach to what were once referred to as expanded threats has evolved to meet the challenges posed by programs that are now broadly referred to as spyware.
See Symantec Enterprise Solutions - Symantec's Antispyware Approach
Tracking Cookies:
The above tools will help you to get rid of "Tracking Cookies"
(Third Party Cookies that use personally identifiable information) stored in your PC,
but you should configure your browser to block them.
In the MS Internet Explorer menu: Tools, Internet Options, Privacy (Medium, at least).
A cookie is not a program, it is a very small text file with information that a Web site can store in your PC. A persistent cookie remains when you close your browser. A temporary or session cookie is stored only for your current browsing session, and is deleted from your computer when you close it.
First-party cookies originate on or are sent to the Web site you are currently viewing. If you do not allow first-party cookies, you may not be able to view some Web sites or take advantage of their customization features.
Third-party cookies either originate on or are sent to Web sites different from the one you are currently viewing. Third-party Web sites usually provide some content on the Web site you are viewing. For example, a site may use advertising from third-party Web sites and those third-party Web sites may use cookies. A common use for this type of cookie is to track your Web visits for advertising or other marketing purposes. Third-party cookies can either be persistent or temporary.
A Web site only has access to the personally identifiable information that you provide to it, such as your log-in and preferences when visiting that site. Normally, only the Web site that created a cookie can read it.
Your Internet Service Provider (ISP) assigns your PC an IP (Internet Protocol) address when you make a connection. An IP address is unique in the whole world at any time, and only your ISP can associate it with your PC at a particular time.
Local Shared Objects:
Adobe Flash Player is the standard for delivering high-impact, rich Web content.
Adobe recommends that all Adobe Flash Player users upgrade to the most recent version of the Player through the Adobe Flash Player Download Center to take advantage of security updates.
Users of Adobe Flash Player on all supported platforms can manually check whether their installed Flash Player is the latest,
most secure version at
Adobe Flash Player - Version Information.
Test with Secunia Personal Software Inspector (PSI).
A local shared object, sometimes referred to as a "Flash cookie",
is a small data file that can be created on your computer by websites containing Adobe Flash Player.
See
Adobe Flash Player - Communicate with Internet
The Adobe Flash Player Settings panels let you make decisions about privacy,
data storage on your computer, security, notifications of updates,
and the use of the camera and microphone installed on your computer.
Use the links in the table of contents to learn how to make these decisions.
See Adobe Flash Player Help
Flash Player provides a number of ways you can manage a website's ability to store information in local shared objects.
You can control storage space by individual websites or for all websites.
See
Adobe Flash Player - TechNote - How to manage and disable Local Shared Objects
A third-party local shared object, sometimes referred to as a "third-party Flash cookie",
is a shared object created by third-party content,
content that is not actually from the site you are currently viewing.
Third-party local shared objects may be important for privacy
because they can be used to track your preferences or your usage across different websites that you visit.
See
Adobe Flash Player - TechNote - How to disable third-party local shared objects
Note that if you have installed the PPAPI version of Flash Player, you must use the Flash Player Native Control Panel to configure your settings. Otherwise, use the Windows Control Panel - Flash Player Settings Manager.
The most severe unpatched Secunia advisory affecting the Adobe Flash Player, with all vendor patches applied,
is rated Highly critical; Do not browse untrusted sites, or disable the Adobe Flash Player.
See Secunia Security Advisories
Delete Flash Local Shared Objects (Flash Cookies) with Objection
[Trevor Hobson, from mozdev.org] (requires Mozilla Firefox)
.sol Editor opens, removes or creates a Macromedia Flash shared object file (.sol),
displays the content of the file and allows you to change the values.
See .sol Editor (Flash Shared Object) (from SourceForge.net)
See Wikipedia - Local Shared Object
Rootkits:
A rootkit is a component that uses stealth to maintain a persistent and undetectable presence on the machine. Actions performed by a rootkit, such as installation and any form of code execution, are done without end user consent or knowledge.
Rootkits do not infect machines by themselves like viruses or worms,
but rather, seek to provide an undetectable environment for malicious code to execute.
To manually install rootkits,
attackers will typically leverage vulnerabilities in the target machine, or use social engineering techniques.
In some cases, rootkits can be installed automatically upon execution of a virus or worm,
or by browsing to a malicious website.
A virus, worm, backdoor or spyware program could remain active and undetected in a system for a long time if it uses a rootkit. The malware may remain undetected even if the computer is protected with state-of-the-art antivirus. And the antivirus can't remove something that it can't see.
The Sinowal Trojan, also known as Torpig and Mebroot, may be one of the most pervasive and advanced pieces of crimeware ever created by fraudsters. Dating back as early as February 2006, the Sinowal Trojan has compromised and stolen login credentials from approximately 300,000 online bank accounts as well as a similar number of credit and debit cards. Other information such as e-mail and FTP accounts from numerous websites, have also been compromised and stolen. Leading anti-virus vendors have indicated that the Sinowal Trojan is specific to Windows XP operating environments.
Once installed, an attacker can perform virtually any function on the system to include remote access, eavesdropping, as well as hide processes, files, registry keys and communication channels.
A good antivirus program, like the AVG Free Antivirus & Malware Protection should detect a rootkit not yet installed. To detect and eliminate one that has been able to install, you can use the Sophos Anti-Rootkit, and the Trend Micro Rootkit Buster (Free).
See
Rootkits - A New Malware Trend (Emsisoft Blog, EMSI Software),
Symantec Security Response - Windows Rootkit Overview
(.pdf, Adobe Acrobat Reader),
Your Botnet is My Botnet - Taking over the Torpig Botnet
(The Computer Security Group at UC Santa Barbara),
Zeus Trojan (EMC Glossary).
Java and ActiveX:
Internet agents, such as Java or ActiveX, contain executable code that is a potential virus
risk, though the problem is minimal at this moment if you keep them updated.
Do not use ActiveX applications from untrusted sources.
Visit Java Download to download and install the latest available version of the Java Runtime Environment (JRE). Then uninstall any older, vulnerable versions. JRE version 7 is now available.
"The nightmare scenario for Mac owners is here.
At least 600,000 Macs worldwide have been infected, silently, by the Flashback Trojan, with no user interaction required.
Here's why this is just the beginning of a long-term problem."
"The current exploit is triggered by a known flaw in Java, which was installed on every copy of OS X until the release of Lion (OS X 10.7) last summer. The flaw was reported in January and patched by Oracle in February, but the Apple version of Java didn't get a patch until early April. So for several months, every Mac owner was vulnerable unless they took specific steps to remove or disable Java."
"If you use any version of OS X before Snow Leopard (10.6) and you have Java installed (all versions of OS X before 10.7 include Java by default), you are vulnerable to this exploit and there is no patch available." [Disabling Java, or updating to OS X 10.7, is recommended]
See
New Mac malware epidemic exploits weaknesses in Apple ecosystem
(ZDNet, Ed Bott. April 6, 2012)
See
Trojan-Downloader: OSX/Flashback.k
(Test and Manual Removal, F-Secure)
Apple today released an update to its Java component [in OS X 10.5 and 10.6] that removes known versions of the Flashback malware.
In a separate study, Symantec reported that it counted only 270,000 infected Macs, down from a high of 600,000 last week.
See
Apple releases Flashback removal tool, infections drop to 270,000
(ZDNet, Ed Bott. April 12, 2012)
Last week's reports of a sharp decline in infections by the Flashback malware may have been premature.
A new report by Dr. Web says 566,000 Macs are still infected, with new infections appearing daily.
See
Russian security firm says Flashback infection rates still high
(ZDNet, Ed Bott. April 20, 2012)
A pair of high-profile malware attacks have given Apple a crash course in security response.
Based on recent actions, 70 million current Mac owners have a right to expect much more from Apple than they're getting today.
See
Flashback malware exposes big gaps in Apple security response
(ZDNet, Ed Bott. April 29, 2012)
Malicious JavaScript:
Malicious scripting attacks are a threat to Web users. A Web site can use a scripting language, like JavaScript, to exploit security vulnerabilities that could allow it to perform installations of spyware or remote control programs.
Firefox, Internet Explorer 7 and Opera have some features to prevent these exploits,
including pop-up warnings that let the user know when a Web site uses scripting.
But these all/nothing controls are not flexible enough.
You should allow the execution of JavaScript only from trusted Web sites.
But typically, a Web site will present scripts coming from other Web sites.
The NoScript Firefox extension provides extra protection for
Firefox,
and other Mozilla-based browsers:
This free, open source add-on allows potentially dangerous JavaScript, Java, Flash and other plugins
to be executed only from trusted Web sites of your choice (e.g. your online bank).
Cross Site Scripting:
Cross-site scripting (XSS) attacks occur when an attacker uses a Web application to send malicious code, generally in the form of a browser side script, to a different end user. Flaws that allow these attacks to succeed are quite widespread and occur anywhere a Web application uses input from a user in the output it generates without validating or encoding it.
An attacker can use XSS to send malicious script to an unsuspecting user. The end user's browser has no way to know that the script should not be trusted, and will execute the script. Because it thinks the script came from a trusted source, the malicious script can access any cookies, session tokens, or other sensitive information retained by your browser and used with that site. These scripts can even rewrite the content of the HTML page.
See Cross Site Scripting Open Web Application Security Project (OWASP)
See Cross-site scripting (Wikipedia)
See XSS (Wikipedia)
Malicious HTML Tags Embedded in Client Web Requests:
None of the solutions that Web users can take are complete solutions. In the end, it is up to Web page developers to modify their pages to eliminate these types of problems.
However, Web users have two basic options to reduce their risk of being attacked through this vulnerability.
The first, disabling scripting languages in their browser,
provides the most protection but has the side effect for many users of disabling functionality that is important to them.
Users should select this option when they require the lowest possible level of risk.
The second solution, being selective about how they initially visit a Web site,
will significantly reduce a user's exposure while still maintaining functionality.
Users should understand that they are accepting more risk when they select this option,
but are doing so in order to preserve functionality that is important to them.
See Malicious HTML Tags Embedded in Client Web Requests CERT Advisory CA-2000-02
Security information is of a time critical nature.
The
Symantec Security Advisories
contain information about major security developments, including Symantec's response to the situation.
A Final Warning
Attackers are moving away from large, multipurpose attacks on network perimeters and towards smaller,
more focused attacks on desktop computers.
The new threat landscape will likely be dominated by emerging threats such as robot networks (botnets),
customizable modular malicious code, and targeted attacks on Web applications and Web browsers.
See Symantec Enterprise Solutions - Internet Security Threat Report
During 2007 the number of samples of malicious code has doubled,
having taken 20 years to reach the size it was at the beginning of this year.
One of the most successful "botnets" of 2007 has been "Storm". The Storm botnet, estimated now to contain millions of compromised computers, has advanced defenses.
See Cracking open the cybercrime economy (CNET News, Dec 14, 2007)
Spoofed e-mails (also known as Phishing) that appear to be from a supplier
(showing a false From address) can put you in danger.
They normally ask you to navigate to a spoofed Web site (showing a false URL) to provide, update or confirm sensitive personal information. To attract you, they may refer to an urgent situation in your account or a very attractive offer.
Some information that Phishing scams are after:
- Credit or debit card numbers
- PINs or Passwords
- Account Numbers
- Personal ID numbers and other personal data (like names and addresses)
Even if you don't provide what they ask for, simply clicking on the link could subject you to "silent" installations of key logging software or backdoor programs.
Many of these sites open spoofing windows to obtain your authorization for an installation. Close them using the X in the upper-right corner of the window. Do not use the controls in these windows; a button can do anything, no matter how it is marked.
Consider that a Web page can spoof the contents of both the Address (URL) and Status Bar.
See PhishTank (operated by OpenDNS)
Don't follow links to your suppliers provided in unsolicited e-mail or untrusted Web sites.
Write the known URL yourself and then go to the supplier's Web site.
Always do this for banks, financial services and on-line stores.
Extortion programs [Ransomware] like CTB-Locker
are delivered by e-mail to encrypt the files in your computer and demand payment to obtain the decryption key to recover them.
Don't execute a program delivered by unsolicited e-mail.
See New Windows 10 scam will encrypt your files for ransom (Zack Whittaker, ZDnet. August 3, 2015)
To navigate the Web, your browser requires access to a DNS (Domain Name Server) service that translates the URLs you type
(i.e. www.somedomain.com) into a set of 4 numbers that is the actual IP (Internet Protocol) address of the Website.
But generally, DNS servers are only directly available from connections provided by the ISP to which they belong.
This means you are generally limited to directly using
the DNS server of your Internet Service Provider (ISP).
If your DNS service directs a certain URL to your own PC, this URL is blocked,
and you get a 404 Error (page not found).
![]() Avoiding the blockage requires using a public DNS service,
like OpenDNS (Free),
Avoiding the blockage requires using a public DNS service,
like OpenDNS (Free),
which also offers an anti-Phishing service.
Additionally, using OpenDNS
guarantees your movements on the Web can not be tracked through the DNS use log at your ISP.
When OpenDNS is unable to determine how to resolve a URL (for example, a typo which is not in our "errors we can fix" list), then OpenDNS provides search results that are the best match for the information provided.
To try it out:
* Read the configuration instructions
* Configure your network settings to use the IP addresses 208.67.222.222 and 208.67.220.220 as your DNS servers
Google Public DNS
is a free, global Domain Name System (DNS) resolution service,
that you can use as an alternative to your current DNS provider.
To try it out:
* Read the configuration instructions
* Configure your network settings to use the IP addresses 8.8.8.8 and 8.8.4.4 as your DNS servers
State of the Internet: Old worms live on; Delaware speediest state; South Korea a broadband king
ZDNet Blogs, May 29th, 2008. Posted by Larry Dignan @ 4:55 am
Akamai [a global server network that handles 20% of the world's total Web traffic] on Thursday [May 29 '08] released its first State of the Internet report and found attack traffic - viruses, worms, bots and such - derived from 125 countries, with 30% of that traffic coming from the United States and China. Some of these attacks, which occurred in the first quarter, were from worms like the Blaster back in 2003.
Of that attack traffic, the top 10 countries accounted for 75% of the attacks. The surprising hotspots for attacks included Venezuela, Argentina and Brazil - three places not exactly known for their hacking communities. Russia was a no-show.
Here's the chart from Akamai's report, which requires registration:
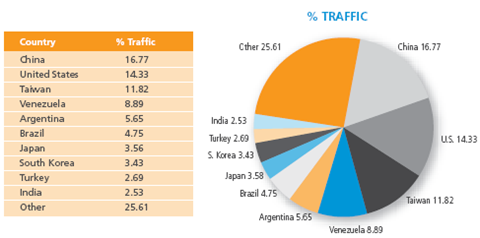
See Akamai Report: The State of the Internet
- 1st Quarter 2008, 2nd Quarter 2008
Have you ever seen a strange security message pop up like an advertisement while you're surfing the web?
Have you seen an unexpected balloon message appear from an unknown program on your system,
telling you that you're infected with a new threat?
These are common tactics used by a type of program Symantec calls "misleading applications"
and other people refer to as "Rogue Software" or "Rogue Anti-Virus".
These programs typically sneak onto their victims' systems while they surf the web,
masquerade as a normal Microsoft Windows alert, or otherwise trick people into downloading them onto their computer.
Once installed,
misleading applications exaggerate or make false claims about the security status or performance of your system,
then promise to solve these bogus problems if you pay them.
See Fake App Attack: Misleading Application Suspicious Notification (Symantec - Norton)
Never accept to install an antivirus or security program that offers itself unexpectedly.
Never accept to install a program that promises to investigate the communications accounts of your contacts.
Websense 2015 Threat Report:
The human and technical aspects of cyber threats changed dramatically in 2014. Highly evasive attacks, created from blended techniques, exploited vulnerabilities and opened cracks in old infrastructure standards. The constant evolution of technology development created a completely new set of challenges.
The Threat Report by Websense Security Labs, provides advice, actionable intelligence and guidance in dealing with existing and emerging threats, taking into account the need for companies to grow and innovate, while protecting intellectual property and confidential information.
There are eight trends definitely worth noting due to the significant risk they pose for data theft this year. These are reviewed across two categories: human behavioral trends and technique-based trends, to examine who's doing what and how they are doing it.
Download the Report:
Register now to gain executive visibility of key security trends and specific guidance in optimizing processes,
policies and security tool usage.
You will also get access to the recorded webcast events, with our security experts discussing the impact and future implications of these trends and threats.
See Websense Security Labs report - 2015 Threat Report
My specialty is Personal Computing and I work as an independent consultant.
Updated: October 14 '15
Castellano: Sección sobre Seguridad de PCs
Back: Home Page (PC Security and Updating Service)
Messages:
Andrés Valencia: Communications